Data In Motion: The Key to COMSEC
Share
Communications Security, or COMSEC, is one of those deep topics. Its not a clean, neat answer in nearly any case, with the caveat given most often "it depends". Whatever the purpose is behind your communications, some degree of COMSEC has to be employed. Those three distinct purposes I defined in The Guerrilla's Guide to the Baofeng Radio as being:
- Sustainment: Sustaining qualities of life; emergency services, etc
- Tactical: Supporting / coordinating fire and maneuver
- Clandestine: Covert instruction / coordination among an Underground
The method by which each of these roles are filled vary widely. So-called experts get hung up on various pieces of equipment and its capabilities (or the lack thereof) baked in, always forgetting the most important part:
DATA IN MOTION IS THE TARGET OF SIGNALS INTELLIGENCE.
Whatever the medium may be in passing the data from point A to point B, it is imperative to recognize data in motion is the actual target of signals intelligence. What is not transmitted is not intercepted. If that transmission is short enough, no matter what's actually transmitted, its also not likely to be intercepted. If no discernible pattern is observed on part of the Signals Intelligence (SIGINT) Team, it is likely they'll miss the transmitted data by simple oversight. Last, if that data in motion is transmitted in such a way that it requires the message in its entirety to decode, it is likely that COMSEC is preserved.
SIGINT teams function at two levels simultaneously - tactical exploitation, meaning real time decision making based on what's intercepted, and pattern analysis, done at a higher echelon over a long period of time for the purpose of predicting an enemy's next moves based on historical behavior patterns.The former can be anything from interception of voice traffic to awareness of threats within a battlespace, the latter through analysis of previous actions. But all of this is done in the effort to, and as a result of, exploitation that very same data in motion. Without it, the SIGINT role is fruitless.
That leads us to understanding that the brevity and obfuscation of data in motion is the real key to COMSEC, with forms of encryption serving to strengthen the preservation of that data should it be intercepted. This is not to dismiss the role of encryption; quite the opposite, in fact; but it is an assertion of the reality that COMSEC begins and ends with keeping a communications plan strictly disciplined in any of the three roles of communications, transmitting only when necessary, and keeping those to short bursts under 5 seconds. Failure to do so will absolutely lead to interception by even novice SIGINT Low-Level Voice Intercept (LLVI) teams and absolutely by airborne platforms.
Once the data in motion has been found, SIGINT teams begin specifically searching for the geolocation of:
- The Point Of Origin (POO)
- The Recipient
The first is most critical and the easiest to target through triangulation should they transmit long enough or get overly chatty at the tactical level. Their use of electronic encryption is irrelevant, their signal gives them away to anyone with the proximity and means to intercept and get a bearing. The Recipient is more difficult, unless they're complete idiots, transmitting a response on the same frequency and via the same recognizable pattern or method.
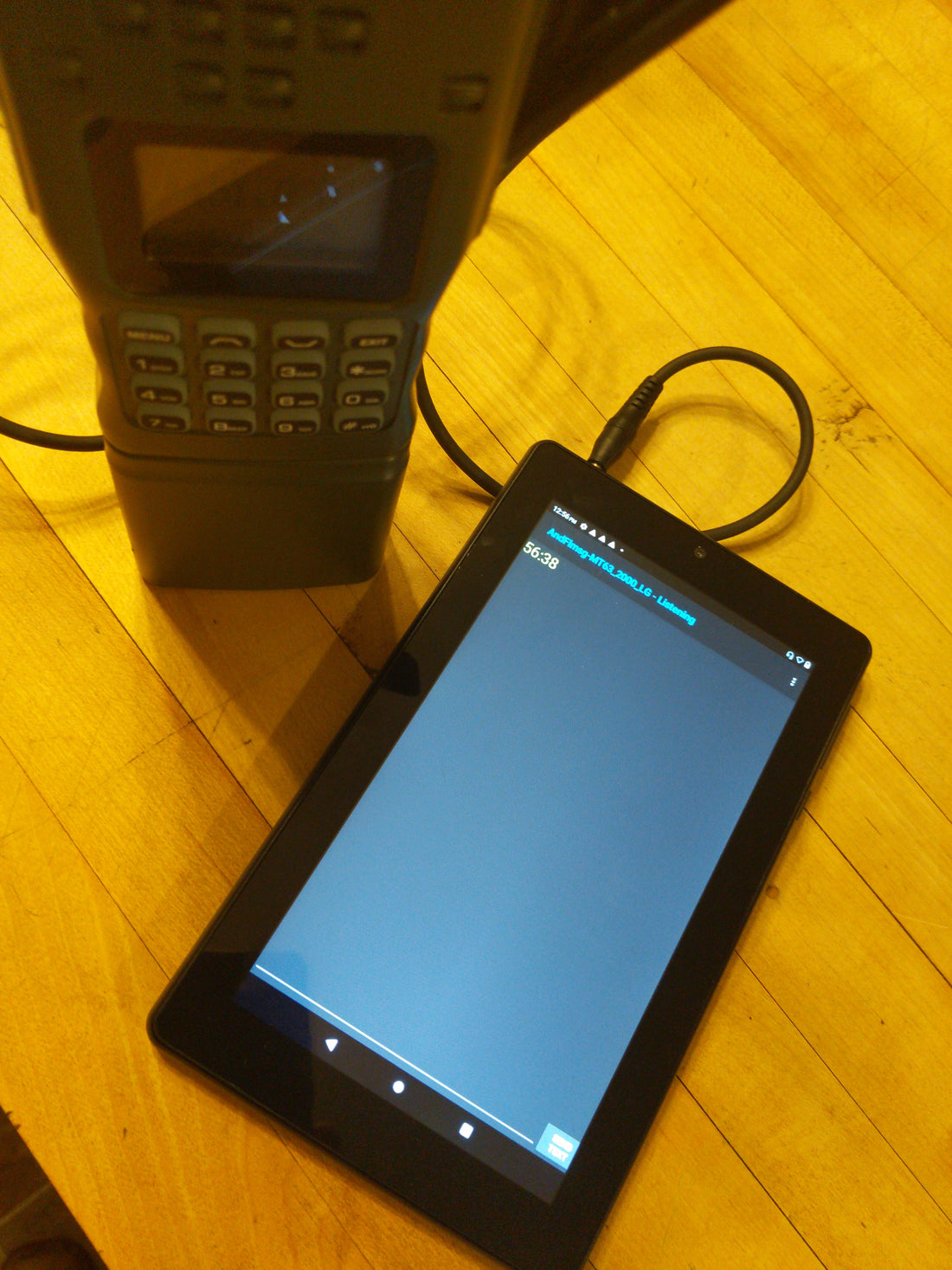
In The Guerrilla's Guide to the Baofeng Radio I cover exactly how to do that with inexpensive components. A radio, of course, a K1 cable, a tablet, and free software. The techniques described in the book can work for nearly any communications means; any radio, any type. It is not isolated to the Baofeng alone.
From the SIGINT side, recognizing that interception of data in motion is the first task, one of the best tools available today is the TinySA spectrum analyzer. The ability to visualize broad swaths of the radio spectrum at once looking for those spikes that indicate something's transmitting - coupled with a waterfall to identify what type of signals are being transmitted - any signal, analog or digital, has a unique visualization to it. When paired with a communications receiver and recorder for audio output, capturing that data in motion, followed by triangulation of the POO, expedites the process of targeting an enemy's communications.
All of this requires training in the real world. While intelligence and communications tasks are fun topics of conversation, even the most knowledgeable out there find themselves coming up short when the real-world application is lacking. Both the Signals Intelligence and Tactical Signals Exploitation Courses should be your first stop for professional instruction.
I'll see you out there. Stay dangerous, stay free. -NCS
